你的KVM小鸡除了能够吃灰以外,还能拿来生小鸡!今天给各位带锅们介绍一下这个玩法,流程很简单,稍微有点Linux基础都应该可以看懂。。
你可曾知道,你曾经买过的某些Xen/OpenVZ小鸡,可能是在KVM里面生出来的?
先简单确定一下你的VPS是否支持此玩法:
lscpu | grep Virt
回显如下,说明你可以继续往下看这篇文章:
Virtualization type: full
更新系统/安装依赖包:
apt -y update apt -y dist-upgrade apt -y install xen-hypervisor-4.8-amd64 xen-tools bridge-utils net-tools
这里有一个包应该和xen-hypervisor-4.8-amd64是等效的,但我不能完全确定:xen-system-amd64
更新Grub:
dpkg-divert --divert /etc/grub.d/08_linux_xen --rename /etc/grub.d/20_linux_xen update-grub
重启VPS使其加载Xen的内核:
reboot
机器没爆炸还能登录上来的话,你现在可以检查Xen状态:
xl info
有类似如下回显说明正常:
host : li1609-54 release : 4.9.0-9-amd64 version : #1 SMP Debian 4.9.168-1+deb9u3 (2019-06-16) machine : x86_64 nr_cpus : 1 max_cpu_id : 0 nr_nodes : 1 cores_per_socket : 1 threads_per_core : 1 cpu_mhz : 2300 hw_caps : 078bfbff:f7fa3203:2c100800:00000121:00000001:001c0fbb:00000000:00000000 virt_caps : total_memory : 1023 free_memory : 63 sharing_freed_memory : 0 sharing_used_memory : 0 outstanding_claims : 0 free_cpus : 0 xen_major : 4 xen_minor : 8 xen_extra : .5 xen_version : 4.8.5 xen_caps : xen-3.0-x86_64 xen-3.0-x86_32p xen_scheduler : credit xen_pagesize : 4096 platform_params : virt_start=0xffff800000000000 xen_changeset : xen_commandline : placeholder cc_compiler : gcc (Debian 6.3.0-18+deb9u1) 6.3.0 20170516 cc_compile_by : ijackson cc_compile_domain : chiark.greenend.org.uk cc_compile_date : Fri Jan 11 18:02:57 UTC 2019 build_id : 9a71c39470d087c0c9fa0d33c04d985ea08aaa04 xend_config_format : 4
编辑Xen配置文件:
nano /etc/xen/xend-config.sxp
确保在这个配置文件内,如下两行是这样的(4.8版本的Xen默认这两行就是这样):
# (network-script network-bridge) (vif-script vif-bridge)
然后取消这两行的注释:
(network-script network-nat) (vif-script vif-nat)
重启Xend:
systemctl restart xend
找到自己小鸡的网关IP:
netstat -r -n
例如我的:
Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface 0.0.0.0 139.162.125.1 0.0.0.0 UG 0 0 0 eth0 139.162.125.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
同时找到自己小鸡的子网掩码:
ifconfig
例如我的:
eth0: flags=4163mtu 1500 inet 139.162.125.54 netmask 255.255.255.0 broadcast 139.162.125.255 inet6 fe80::f03c:91ff:fe9a:f00 prefixlen 64 scopeid 0x20 inet6 2400:8902::f03c:91ff:fe9a:f00 prefixlen 64 scopeid 0x0 ether f2:3c:91:9a:0f:00 txqueuelen 1000 (Ethernet) RX packets 697 bytes 315320 (307.9 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 445 bytes 71363 (69.6 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
现在编辑网卡配置文件:
nano /etc/network/interfaces
我的默认是使用的DHCP:
allow-hotplug eth0 iface eth0 inet dhcp
改桥接以及配置NAT(第一套方案):
allow-hotplug eth0
iface eth0 inet manual
auto xenbr0
iface xenbr0 inet static
address 139.162.125.54
netmask 255.255.255.0
gateway 139.162.125.1
bridge_ports eth0
auto xenbr1
iface xenbr1 inet static
address 192.168.0.1
netmask 255.255.255.0
bridge_ports none
bridge_stp off
bridge_fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.0.0/24' -o xenbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.0.0/24' -o xenbr0 -j MASQUERADE
这套方案是桥接/NAT都能使用,如果你的小鸡有多个独立IP,那么待会创建小鸡的时候把网卡桥到xenbr0上面,如果小鸡只有一个独立IP,那么就桥到xenbr1上面用NAT。当然有些小鸡改桥接可能一重启网卡就会挂,再加上一般的VPS也没有多IP,那么你可以使用下面这套方案。
纯NAT(第二套方案):
allow-hotplug eth0
iface eth0 inet static
address 139.162.125.54
netmask 255.255.255.0
gateway 139.162.125.1
auto xenbr0
iface xenbr0 inet static
address 192.168.0.1
netmask 255.255.255.0
bridge_ports none
bridge_stp off
bridge_fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.0.0/24' -o eth0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.0.0/24' -o eth0 -j MASQUERADE
当然我这边还是使用的第一套方案,配置好了之后现在重启网络服务:
systemctl restart networking.service
我的建议是既然改了Xen配置又改了网卡配置,用systemd去重启这些服务并不妥当,很有可能会报错,干脆再重启一遍VPS:
reboot
上来之后检查网桥状态:
brctl show
回显如下表示网桥正常:
bridge name bridge id STP enabled interfaces xenbr0 8000.005056001a72 no ens18 xenbr1 8000.000000000000 no
同时查看网卡信息,第一套方案的网卡信息应该是这样的:
root@localhost:/etc/network# ifconfig eth0: flags=4163mtu 1500 ether f2:3c:91:9a:0f:00 txqueuelen 1000 (Ethernet) RX packets 189 bytes 18682 (18.2 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 133 bytes 21063 (20.5 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73 mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10 loop txqueuelen 1 (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 xenbr0: flags=4163 mtu 1500 inet 139.162.125.54 netmask 255.255.255.0 broadcast 139.162.125.255 inet6 fe80::f03c:91ff:fe9a:f00 prefixlen 64 scopeid 0x20 inet6 2400:8902::f03c:91ff:fe9a:f00 prefixlen 64 scopeid 0x0 ether f2:3c:91:9a:0f:00 txqueuelen 1000 (Ethernet) RX packets 171 bytes 14479 (14.1 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 134 bytes 21181 (20.6 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 xenbr1: flags=4163 mtu 1500 inet 192.168.0.1 netmask 255.255.255.0 broadcast 192.168.0.255 inet6 fe80::d4f9:78ff:fe32:9fc9 prefixlen 64 scopeid 0x20 ether d6:f9:78:32:9f:c9 txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 9 bytes 718 (718.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
而第二套方案的网卡信息应该是:
eth0: flags=4163mtu 1500 inet 139.162.125.54 netmask 255.255.255.0 broadcast 139.162.125.255 inet6 fe80::f03c:91ff:fe9a:f00 prefixlen 64 scopeid 0x20 inet6 2400:8902::f03c:91ff:fe9a:f00 prefixlen 64 scopeid 0x0 ether f2:3c:91:9a:0f:00 txqueuelen 1000 (Ethernet) RX packets 497 bytes 47926 (46.8 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 328 bytes 52043 (50.8 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73 mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10 loop txqueuelen 1 (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 xenbr0: flags=4163 mtu 1500 inet 192.168.0.1 netmask 255.255.255.0 broadcast 192.168.0.255 inet6 fe80::f855:faff:fe60:b371 prefixlen 64 scopeid 0x20 ether fa:55:fa:60:b3:71 txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 7 bytes 578 (578.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
现在我们需要创建虚拟机镜像,这边我以Debian9为例,使用的网络模式是NAT(第一套方案):
xen-create-image --hostname=imlala-test --vcpus=1 --memory=512mb --size=5g --dir=/opt/images --bridge=xenbr1 --ip=192.168.0.2 --netmask=255.255.255.0 --gateway=192.168.0.1 --pygrub --dist=stretch
在镜像创建过程中,你将可以看到类似这样的回显:
General Information
--------------------
Hostname : imlala-test
Distribution : stretch
Mirror : http://httpredir.debian.org/debian
Partitions : swap 512M (swap)
/ 5g (ext4)
Image type : sparse
Memory size : 1024mb
Bootloader : pygrub
Networking Information
----------------------
IP Address 1 : 192.168.0.2 [MAC: 00:16:3E:6D:7A:AE]
Netmask : 255.255.255.0
Gateway : 192.168.0.1
一旦镜像创建成功,你将得到该镜像的ROOT密码,这个要自己保存好:
Installation Summary --------------------- Hostname : imlala-test Distribution : stretch MAC Address : 00:16:3E:6D:7A:AE IP Address(es) : 192.168.0.2 SSH Fingerprint : SHA256:0noXFqcSFuzp4JC6/oxAnfJVMhQ9RGRXM/QMsBc5Lfw (DSA) SSH Fingerprint : SHA256:c92Vgs2rEaBCSAPNXMat4yDfpN9bvq2XLmahI3aq/bM (ECDSA) SSH Fingerprint : SHA256:JIUiqFGT8TIzhLpYOVRHUxJn9N6lCd9bMBejFlQZcpo (ED25519) SSH Fingerprint : SHA256:JbrrjPz5Ih+yF6KKcROilWGwbxL7gt4YsmNbpkWl0pk (RSA) Root Password : www.lala.im
现在列出所有虚拟机镜像:
xen-list-images
你将看到之前创建镜像所生成的cfg文件:
Name: imlala-test Memory: 512 MB IP: 192.168.0.2 Config: /etc/xen/imlala-test.cfg
使用cfg文件启动虚拟机:
xl create /etc/xen/imlala-test.cfg
如果没有任何报错,那么虚拟机应该已经启动成功,使用下面的命令检查(恭喜你,撒花):
xl list
回显如下:
Name ID Mem VCPUs State Time(s) Domain-0 0 490 1 r----- 220.1 imlala-test 1 512 1 ------ 2.0
此时我们就可以通过控制台进入虚拟机了:
xl console imlala-test
在控制台内,我们需要更改SSH的配置以允许ROOT用户登录:
nano /etc/ssh/sshd_config
将
#PermitRootLogin prohibit-password #PasswordAuthentication yes
改为:
PermitRootLogin yes PasswordAuthentication yes
重启SSH:
systemctl restart sshd
按键盘组合键Ctrl+]退出Console,回到母鸡(VPS)内进行端口转发,将小鸡的22端口转发到母鸡(VPS)的23333端口:
iptables -t nat -A PREROUTING -p tcp -m tcp --dport 23333 -j DNAT --to-destination 192.168.0.2:22
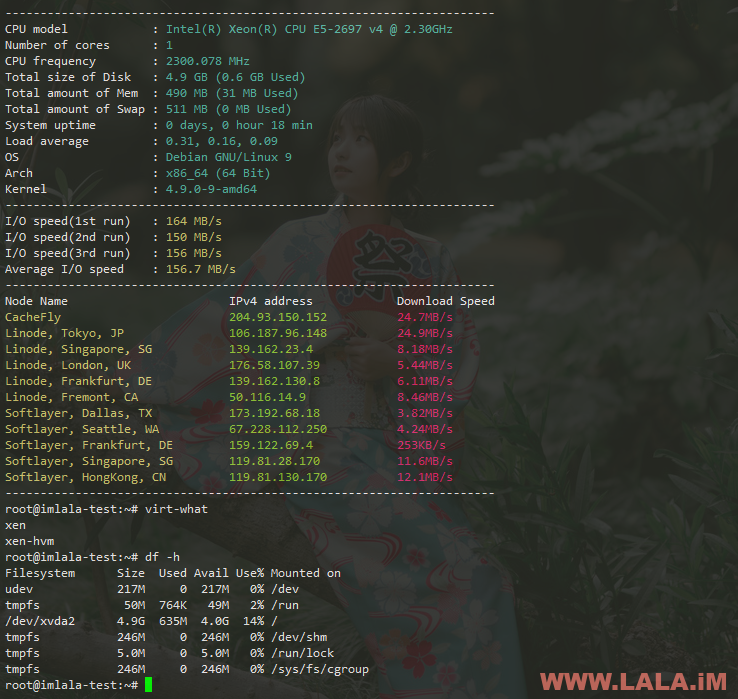
现在使用母鸡(VPS)的IP:23333即可登录到这台小鸡内,这里上一张小小鸡的简单测评,毕竟是虚拟化里面再进行虚拟化,性能损失的比较严重:
Xen更多常用的管理命令:
xl shutdown imlala-test xl destroy imlala-test xl reboot imlala-test
删除镜像,有多种方法,如果是使用本文的方法创建的镜像,那么是直接删除目录,如果是通过LVM逻辑卷创建的,指定对应的VG:
xen-delete-image --hostname=imlala-test --dir=/opt/images xen-delete-image --hostname=imlala-test --lvm=vg_imlala
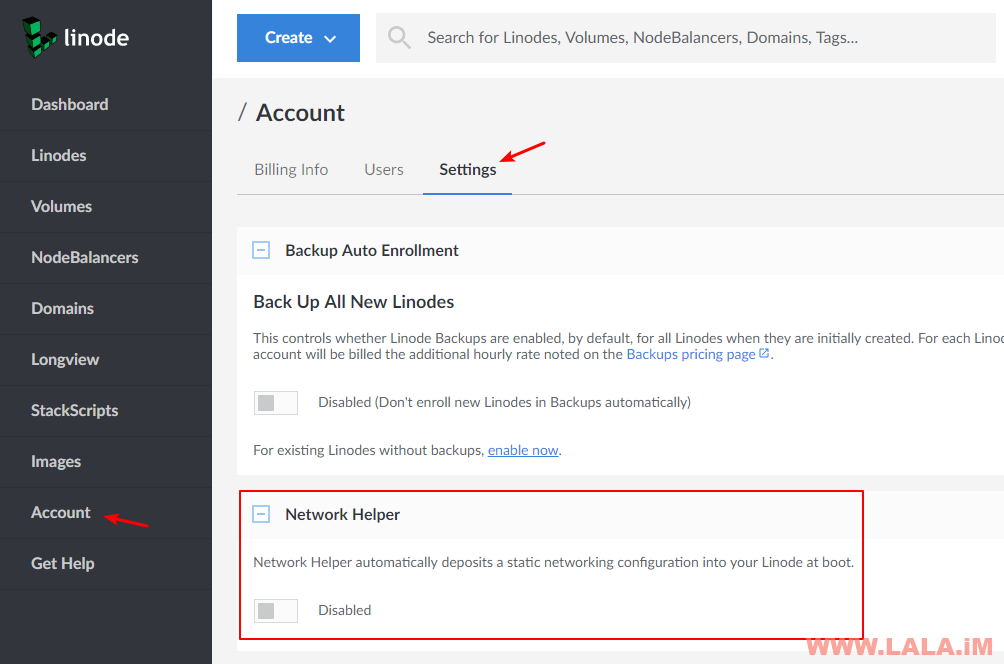
额外说一下,如果你和我一样是在Linode内玩这种骚操作,你需要先将Linode的Network Helper给关闭,否则网卡改了也是白改,重启会自动给你还原:





最新评论
5211314
能不能教我 一点不会