在这篇文章之后:https://lala.im/9147.html,我突然又想到sing-box(以下简称sb)的出站是支持wireguard(以下简称wg)的。
如果只是要解锁某些东西的话,那应该也可以先试试warp的ip吧,如果warp的ip能解的话,那不就省了个落地鸡的钱了?
最终我配置完成后,测试确实可以解,当然我觉得这个还是有点运气成分的,正好warp分配给我的这个ip比较给力,不过好像看网上说也有办法刷ip?但是我试了下始终给我分配的就那一个ip。。不过也足够了,反正现在能解就行。。
然后就是在配置的过程中,我发现了两个非常好用的工具,这里分享一下。
第一个是MediaUnlockTest:https://github.com/HsukqiLee/MediaUnlockTest
这个测解锁的工具是基于lmc999的版本用go重写的,检测速度快的一匹,而且还支持更多的检测项目,但是好像用的人不多= =给大伙推荐一下= =
然后是wgcf-cli:https://github.com/ArchiveNetwork/wgcf-cli
它只是名字很像wgcf,但和wgcf是两个完全不同的项目,这个工具可以直接生成sb的json配置文件,省时省力= =
ok下面记录下配置方法,首先还是先在机器上安装sb:
bash <(curl -fsSL https://sing-box.app/deb-install.sh)
然后把刚才说的wgcf-cli安装一下:
apt -y update apt -y install zstd mkdir wgcf-cli && cd wgcf-cli curl -L https://github.com/ArchiveNetwork/wgcf-cli/releases/download/v0.3.6/wgcf-cli-linux-64.tar.zstd -o wgcf-cli-linux-64.tar.zstd tar -xvf wgcf-cli-linux-64.tar.zstd
执行如下命令注册warp账户:
./wgcf-cli register
然后生成sb的配置文件:
./wgcf-cli generate --sing-box
在当前目录下面会有一个wgcf.sing-box.json文件,里面的内容类似:
{
"type": "wireguard",
"tag": "wireguard-out",
"server": "engage.cloudflareclient.com:2408",
"server_port": 2408,
"local_address": [
"172.16.0.2/32",
"2606:4700:110:8cc4:5177:d2b5:fd92:a1cb/128"
],
"private_key": "hidden",
"peer_public_key": "hidden",
"reserved": "/oNV",
"mtu": 1280
}
然后把这个生成出来的配置进行一点修改。主要做2点修改。
1、把server后面的端口号去掉,不然sb运行会报错。
2、配置使用system_interface,目的是让MediaUnlockTest后续可以测试warp分配到的ip能否解锁。
改成这样就可以了,把改好的配置复制保存一下待会需要用到:
{
"type": "wireguard",
"tag": "wireguard-out",
"server": "engage.cloudflareclient.com",
"server_port": 2408,
"system_interface": true,
"interface_name": "wg0",
"local_address": [
"172.16.0.2/32",
"2606:4700:110:8cc4:5177:d2b5:fd92:a1cb/128"
],
"private_key": "hidden",
"peer_public_key": "hidden",
"reserved": "/oNV",
"mtu": 1280
}
现在有两种配置方式可以实现套warp。第一种是分流,第二种就是链式代理。这里我分别记录下配置方法。
先说第一种分流的情况,编辑sb的配置文件:
nano /etc/sing-box/config.json
这是我的一个示例配置:
{
"log": {
"level": "info"
},
"dns": {
"servers": [
{
"tag": "google",
"address": "tls://8.8.8.8",
"strategy": "ipv4_only"
}
],
"rules": [
{
"outbound": "any",
"server": "google"
}
]
},
"inbounds": [
{
"type": "vless",
"tag": "vless-in",
"listen": "0.0.0.0",
"listen_port": 443,
"sniff": true,
"users": [
{
"name": "imlala",
"uuid": "hidden", // sing-box generate uuid
"flow": "xtls-rprx-vision"
}
],
"tls": {
"enabled": true,
"server_name": "www.python.org",
"reality": {
"enabled": true,
"handshake": {
"server": "www.python.org",
"server_port": 443
},
"private_key": "hidden", // sing-box generate reality-keypair
"short_id": [
"hidden" // sing-box generate rand --hex 8
]
}
}
}
],
"outbounds": [
{
"type": "direct",
"tag": "direct"
},
{
"type": "dns",
"tag": "dns-out"
},
{
"type": "wireguard",
"tag": "wireguard-out",
"server": "engage.cloudflareclient.com",
"server_port": 2408,
"system_interface": true,
"interface_name": "wg0",
"local_address": [
"172.16.0.2/32",
"2606:4700:110:8cc4:5177:d2b5:fd92:a1cb/128"
],
"private_key": "hidden",
"peer_public_key": "hidden",
"reserved": "/oNV",
"mtu": 1280
}
],
"route": {
"rules": [
{
"protocol": "dns",
"outbound": "dns-out"
},
{
"rule_set": [
"geosite-netflix",
"geosite-disney",
"geosite-abema",
"geosite-reddit"
],
"outbound": "wireguard-out"
}
],
"rule_set": [
{
"type": "remote",
"tag": "geosite-netflix",
"format": "binary",
"url": "https://raw.githubusercontent.com/SagerNet/sing-geosite/rule-set/geosite-netflix.srs",
"download_detour": "direct",
"update_interval": "7d"
},
{
"type": "remote",
"tag": "geosite-disney",
"format": "binary",
"url": "https://raw.githubusercontent.com/SagerNet/sing-geosite/rule-set/geosite-disney.srs",
"download_detour": "direct",
"update_interval": "7d"
},
{
"type": "remote",
"tag": "geosite-abema",
"format": "binary",
"url": "https://raw.githubusercontent.com/SagerNet/sing-geosite/rule-set/geosite-abema.srs",
"download_detour": "direct",
"update_interval": "7d"
},
{
"type": "remote",
"tag": "geosite-reddit",
"format": "binary",
"url": "https://raw.githubusercontent.com/SagerNet/sing-geosite/rule-set/geosite-reddit.srs",
"download_detour": "direct",
"update_interval": "7d"
}
]
}
}
启动sb:
systemctl enable --now sing-box
测试下看成功没:
curl --ipv4 --interface wg0 ip.sb
如果回显的是warp的ip则说明ok了。现在就可以用MediaUnlockTest来测试解锁情况了,先下载安装一下:
mkdir unlock-test && cd unlock-test curl -L https://github.com/HsukqiLee/MediaUnlockTest/releases/download/v1.4.9-1720957826/unlock-test_linux_amd64 -o unlock-test_linux_amd64 chmod +x unlock-test_linux_amd64
检测的时候指定wg0这个接口名:
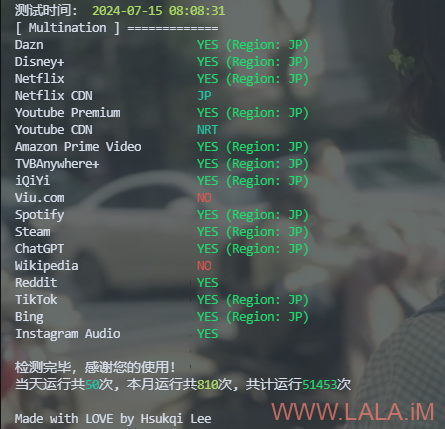
./unlock-test_linux_amd64 -I wg0 -m 4
结果:
再测下机器原本的ip:
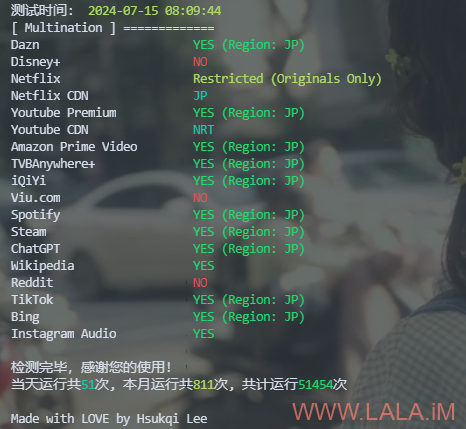
./unlock-test_linux_amd64 -I eth0 -m 4
结果:
和原本的ip对比可以看到warp的ip把迪士尼、奈飞、红迪都解了,还是很不错的。。。
客户端去连接这个机器的vless节点即可,这里就先不给客户端的示例配置了,接下来要介绍的链式代理的客户端配置里面都有,直接参考下面的配置就行。
现在来说一下第二种方法:链式代理。链式代理不需要给服务端的出站配置wg,只需要在服务端搭一个普通的节点就行,下面是一个示例配置:
{
"log": {
"level": "info"
},
"dns": {
"servers": [
{
"address": "tls://8.8.8.8",
"strategy": "ipv4_only"
}
]
},
"inbounds": [
{
"type": "vless",
"tag": "vless-in",
"listen": "0.0.0.0",
"listen_port": 443,
"sniff": true,
"users": [
{
"name": "imlala",
"uuid": "hidden", // sing-box generate uuid
"flow": "xtls-rprx-vision"
}
],
"tls": {
"enabled": true,
"server_name": "www.python.org",
"reality": {
"enabled": true,
"handshake": {
"server": "www.python.org",
"server_port": 443
},
"private_key": "hidden", // sing-box generate reality-keypair
"short_id": [
"hidden" // sing-box generate rand --hex 8
]
}
}
}
],
"outbounds": [
{
"type": "direct"
},
{
"type": "dns",
"tag": "dns-out"
}
],
"route": {
"rules": [
{
"protocol": "dns",
"outbound": "dns-out"
}
]
}
}
链式代理主要是修改客户端的配置文件,把刚才wgcf-cli生成的sb配置写到客户端的配置文件内即可,下面是一个示例配置:
{
"log": {
"level": "info",
"timestamp": true
},
"dns": {
"servers": [
{
"tag": "google",
"address": "tls://dns.google",
"address_resolver": "resolver",
"strategy": "ipv4_only",
"detour": "select"
},
{
"tag": "tencent",
"address": "tls://dot.pub",
"address_resolver": "resolver",
"strategy": "ipv4_only",
"detour": "direct"
},
{
"tag": "resolver",
"address": "223.5.5.5",
"strategy": "ipv4_only",
"detour": "direct"
},
{
"tag": "deniend",
"address": "rcode://refused"
}
],
"rules": [
{
"outbound": "any",
"server": "tencent"
},
{
"clash_mode": "direct",
"server": "tencent"
},
{
"clash_mode": "global",
"server": "google"
},
{
"rule_set": "geosite-geolocation-cn",
"server": "tencent"
}
],
"final": "google"
},
"inbounds": [
{
"type": "tun",
"tag": "tun-in",
"interface_name": "tun0",
"inet4_address": "172.17.0.1/30",
"auto_route": true,
"strict_route": true,
"stack": "mixed",
"sniff": true
}
],
"outbounds": [
{
"type": "selector",
"tag": "select",
"outbounds": [
"fwd",
"wireguard",
"auto"
],
"default": "fwd",
"interrupt_exist_connections": true
},
{
"type": "vless",
"tag": "fwd",
"server": "hidden",
"server_port": 443,
"uuid": "hidden",
"flow": "xtls-rprx-vision",
"tls": {
"enabled": true,
"server_name": "www.python.org",
"utls": {
"enabled": true,
"fingerprint": "chrome"
},
"reality": {
"enabled": true,
"public_key": "hidden",
"short_id": "hidden"
}
}
},
{
"type": "wireguard",
"tag": "wireguard",
"server": "engage.cloudflareclient.com",
"server_port": 2408,
"local_address": [
"172.16.0.2/32",
"2606:4700:110:8cc4:5177:d2b5:fd92:a1cb/128"
],
"private_key": "hidden",
"peer_public_key": "hidden",
"reserved": "/oNV",
"mtu": 1280,
"detour": "fwd"
},
{
"type": "urltest",
"tag": "auto",
"outbounds": [
"fwd",
"wireguard"
],
"url": "https://www.gstatic.com/generate_204",
"interval": "10m",
"interrupt_exist_connections": true
},
{
"type": "direct",
"tag": "direct"
},
{
"type": "block",
"tag": "block"
},
{
"type": "dns",
"tag": "dns"
}
],
"route": {
"rules": [
{
"protocol": "dns",
"outbound": "dns"
},
{
"ip_is_private": true,
"outbound": "direct"
},
{
"clash_mode": "direct",
"outbound": "direct"
},
{
"clash_mode": "global",
"outbound": "select"
},
{
"rule_set": [
"geoip-cn",
"geosite-geolocation-cn"
],
"outbound": "direct"
}
],
"rule_set": [
{
"type": "remote",
"tag": "geoip-cn",
"format": "binary",
"url": "https://raw.githubusercontent.com/SagerNet/sing-geoip/rule-set/geoip-cn.srs",
"download_detour": "select",
"update_interval": "7d"
},
{
"type": "remote",
"tag": "geosite-geolocation-cn",
"format": "binary",
"url": "https://raw.githubusercontent.com/SagerNet/sing-geosite/rule-set/geosite-geolocation-cn.srs",
"download_detour": "select",
"update_interval": "7d"
}
],
"final": "select",
"auto_detect_interface": true
},
"experimental": {
"cache_file": {
"enabled": true
},
"clash_api": {
"external_controller": "127.0.0.1:9090",
"external_ui": "ui",
"external_ui_download_url": "https://github.com/MetaCubeX/Yacd-meta/archive/gh-pages.zip",
"external_ui_download_detour": "select",
"default_mode": "rule"
}
}
}
启动sb后用浏览器访问127.0.0.1:9090,打开yacd的webui,然后选择tag为wireguard的节点就ok了。我个人还是推荐用分流的方式,因为warp有时候速度很拉= =
最后提一嘴,xray-core也是支持wg出站的,现在新版本好像入站也支持wg了,喜欢用xray-core的可以去试试。。







最新评论
5211314
能不能教我 一点不会